There was a bug in earlier versions of the FortiOS software regarding SIP/Lync that was resolved in 4.0 MR3 Patch 3. So make sure your fortigate is updated. Firmware images can be found at http://support.fortinet.com/ with a valid login and support contract.
Once your fortigate is updated to MR3 Patch3 or above. you will also need to configure your fortigate in Interface Mode. this will allow you to use all 4-6-8 interfaces independently. this becomes useful for creating separate networks within the fortigate ie (SIP Trunking, Lync, Development, Internal network etc....)
This can be found by going to System -> Network -> Interfaces, then clicking switch mode at the top. And choosing Interface Mode
Switch Mode Internal=INT1/INT2/INT3/INT4/INT5/INT6
Interface Mode Internal1=INT1, Internal2=INT2, Internal3=INT3, Internal4=INT4, Internal5=INT5, Internal6=INT6
Note: you cannot have anything set on the fortigate for this, all rules need to be deleted before you are able to switch the interface mode. This process is usually performed on Fortigate's right out of the box.
First thing, choose an interface you wish to use for the SIP Trunk. I picked Interface 6. but makes no difference.
Also i configured the interface with a /30 subnet (Point-to-Point) which will allow me only the Fortigate interface and Lync on this interface.
On your Lync server, configure your PSTN/Mediation Interface with the IP Information you configured for your Fortigate Interface.
Note: Also set your interface metric. This will allow the Lync server to always use this interface when making outbound calls. If this is not set it will automatically select the interface, if it selects the wrong one, your calls will fail!
In Topology Builder, set your Primary IP Address and PSTN Address. Once set, Publish your Topology.
By this point, you should already have placed your ITSPs Gateway into your Topology and assigned it to your mediation server. Use the ports and protocol given to you by your provider. We use ThinkTel they use TCP on port 5060.
Back to your Fortigate, here you will create your policies for inbound and outbound rules.
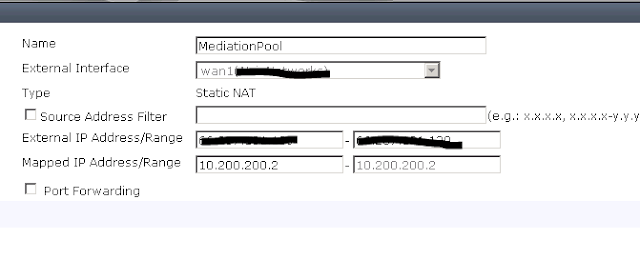
Create a new Virtual IP
Create a new VIP
External IP Address will be the one you plan to give to your SIP Trunking Provider. Again I use different IP Address then the one on all my other Interfaces. for Lync I usually request a /29 from the ISP. Which gives you 6 usable IP Address (1 for SIP Trunk, 1 for meet/dialin, 3 for Lync Edge (sip,av,webconf) and the 6th for the end users to use for NATing out to the Internet. )
Next create you custom Services for your Signaling and Media ports.
Also create a New Address entry for your Mediation PSTN IP Address.
Once you have all that complete, its time for the CLI!!
the below you can copy and paste right into the CLI of your Fortigate.
You will need to disable ALG, and also add 2 entries in the sip session-helper, one for TCP and one for UDP.
config sys session-helper
edit 0
set name sip
set port 5060
set protocol 17
end
And one for TCP
config sys session-helper
edit 0
set name sip
set port 5060
set protocol 6
end
Then create a new Voip UTM Profile (lync)
edit "lync"
set comment "lync voip profile"
config sip
set register-rate 1000
set invite-rate 1000
set log-violations enable
set preserve-override enable
end
config sccp
set log-call-summary enable
set log-violations enable
end
Once the above session-helper and Voip Profile are created, now we can create our Firewall Policies.
First we will create from Internal -> WAN1 so for all outbound calls/signaling. Notice how I did NOT enable UTM. the UTM Voip policy will only be applied from WAN1-> Internal
once you have created both firewall policies, go to your Lync Server and open Internet Explorer and type http://whatismyip.com/. this should display the IP Address you used when creating your VIP above. if it does not, check to make sure you selected your 10.200.200.2 Interface with a metric of 1.
That is all, now you should be able to make and receive calls to Lync via SIP Trunking and your Fortigate.
Happy Calling!!!










Excellent article, thank you!
ReplyDeleteFantastic information here!! I could not have got through my deployment without this. Thanks alot, Great job!!
ReplyDeleteThank you for the great information.
ReplyDeleteWould you happen to know if you configure a collocated Mediation/FrontEnd server with a single NIC and two IP addresses if this will work for outbound calls?
I've configured the Lync server with two internal IPs, set the primary and PSTN connectivity addresses and publsihed my config. Both IPs on that single NIC are on the same subnet - LAN. We have a one to one NAT setup with the provider and they have confirmed using the internal IPs are fine and I don't require a public facing routable address.
My issue is when I make outbound calls, network traces and the logging tool are showing the primary address of the fronEnd pool and the traffic isn't being initiated on the second IP.
Also, with regards to the interface on Fortigate - in my scenario will I have to use an interface allocated on the Fortigate or will the internal second IP work?
Any help will be greatly appreciated.
The SIP Trunking system helps the customers in an incredible manner. Private internet connection gives you advanced security. You are entirely secure in business deals. The SIP Trunking system offers the business PBX installs and helps in use VoIP.
ReplyDeleteThanks!
The best of VoIP systems
ReplyDeletehttp://prostarcomm.com/
There is no doubt that SIP Trunking helps unify your communication strategy and reduces your expenses. Start by doing some research on providers like ThinkTel and decide which one will suit your needs better.
ReplyDeleteI saw your post when it was fresh. I stumbled upon this link while looking for something else. Since this seems to be favored by Google, it is worth pointing out that MS has changed its mind.
ReplyDeleteIn today's Job market, Fortinet's skills are highly recommended. Fortinet offers a growing portfolio of highly sought-after certifications that allow professionals to boost their careers and realize their life ambitions. Examine the following certification classifications and discover the right option for you.
KillerDumps offers you all IT test dump files and practice test simulator at a discounted price with 100% guaranteed success. We provide continuous after-sales support for the question and answer files and the Fortinet practice software to counteract any inconvenience.
You can get Fortinet Exam Dumps
Great job here on. I read a lot of blog posts, but I never heard a topic like this. I Love this topic you made about the blogger's bucket list. Very resourceful. sip.us
ReplyDelete