Lync Me - Unified Communications Blog
Lync and Skype for Business Blog and everything in between
Wednesday 17 June 2015
Skype for Business Hybrid Features
For anyone looking for a comparison of features available when impelemtning Skype for Business Server 2015 in a hybrid configuration, below is a list of available features.
Make note of the ** and *** notes that these are planned features and are not yet available.
Also below outlines the high level prerequisites required for Skype for Business Hybrid.
Tuesday 9 June 2015
Skype for Business New Certificates Request Wizard
Since the first release of Lync 2010 Microsoft has been making some huge improvements right up to the latest release of Skype for Business. With this release a ton of new features and changes that will make this version the best one yet!
In this post I will outline one of the new Skype for Business improvements - Certificates! Something that I have seen just about everyone that has tried to deploy Lync spend hours, days if not weeks trying to get the certificates correct.
When deploying your Skype for Business Server, the deployment is very much the same as Lync 2010/2013 until you click Request!
This new Certificate Request Wizard will simplify the certificate request process by putting all the next, next, next into the same window. All you need to do is fill in the organization details and click next, which will request the new certificate from your internal PKI as shown below.
What if I need to request offline?
Down at the bottom of the certificate request window, click Advanced. This will open the previous version method wizard which will allow you to specify offline request
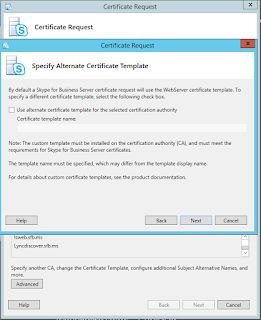
What if I need to specify a custom Certificate Template?
These settings are also found in the advanced settings.
Thursday 7 May 2015
Lync 2013 to Skype for Business In-Place Upgrade Detailed Steps
The process of the Skype for Business In-Place upgrade is a fantastic and quick"er" way of updating to the latest Skype for Business Edition. This post will show detailed how-to on upgrading an Enterprise Pool from Lync 2013 to Skype for Business Server. The process is similar for upgrading Standard Edition Pools and the same principals and concepts apply.
The LAB I am performing this update to is as followed:
The LAB I am performing this update to is as followed:
- 3 Lync 2013 Front End Servers in a pool called lspool01.lmlab-a.com
- 1 SQL 2012 Back-end
- 1 File Share located on Domain Controller
- 15,000 users provisioned on this LAB Lync 2013 pool
After the upgrade the pool will be running Skype for Business Server 2015 running on the same SQL 2012 back-end. In a later post I will document on setting up an Always ON SQL 2014 cluster, but for this post will be a single back end server.
NOTE: As documented in this article https://technet.microsoft.com/en-us/library/dn951388.aspx Windows Server 2008 R2 is no longer recommended to use with Skype for Business Server due to changes and limitations with Server 2008 R2 and Windows Fabric. All 3 of these Front End Servers are running Server 2012 R2.
Testing Purpose: This guide is helpful for upgrading your Lync 2013 pool to Skype for Business Server 2015 using the In-Place Upgrade feature. Before running through these steps in your production environment, test it!. Confirm your topology, servers and services are functional and error free before upgrading.
Production Notice: For anyone doing an In-Place Upgrade in their production environment note that doing this process without moving users to a secondary pool will disrupt users until the upgrade process is complete on ALL front-end servers. It is recommended to either move all your users to a secondary pool before upgrading the primary pool, or schedule a maintenance window.
Also depending on the O/S Lync 2013 is running on, you will need to install these following hot-fix's. If not you will run into issues during the upgrade process. The corresponding hot-fix must be installed on every Lync front-end server you are upgrading.
- Server 2008 R2 - KB 2533623 needs to be installed. Get it here.
- Server 2012 - KB 2858668 needs to be installed. Get it here.
- Server 2012 R2 - KB 2928006 needs to be installed. Get it here.
Also here is a list of other requirements and recommendations prior to doing an In-Place Upgrade:
- Lync Servers must be patched! visit this link for the latest Lync 2013 CU patches - https://support.microsoft.com/en-us/kb/2809243
- All local instances of SQL on Front-End/Edge Servers need to be 2012 SP1+
- Uninstall LRS Admin tool from Lync Server 2013 before running In-Place Upgrade
- Upgrade the topology from the inside to the outside. (pools, edge servers, CMS pool)
- If you use Kerberos authentication for Web Services, you must reassign Kerberos accounts and reset the password after the In-Place Upgrade is complete
- SBA/SBS must be removed from the pool that you are wanting to upgrade. After the update the SBA/SBS can be added back
The process of an In-Place Upgrade must be done from another computer that's joined to the same Active Directory Domain that Lync 2013 is installed in, but cannot have the Lync 2013 Administrative Tools installed. You can use a management PC for this, or another non-Lync server.
STEP 1: Install Administrator Tools and download topology
- From your Management PC/Server Install the Skype for Business Administrator Tools.
- From the installation media run setup from Volume\Setup\AMD64\setup.exe
- On the deployment wizard, install Administrator tools
NOTE: Notice in the screen shot below that Prepare Active Directory is already "Complete". This is because at time of RTM of Skype for Business Server there are NO Active Directory Updates. Continue with clicking Install Administrative Tools.
NOTE: When Installing the Core Components you should connect to the internet and check for updates, this will confirm you are always using the latest CU updates available.
Continue with the installation of the Administrative Tools.
4. From the Start screen, open Skype for Business Server Topology Builder
5. Click Download topology from existing deployment
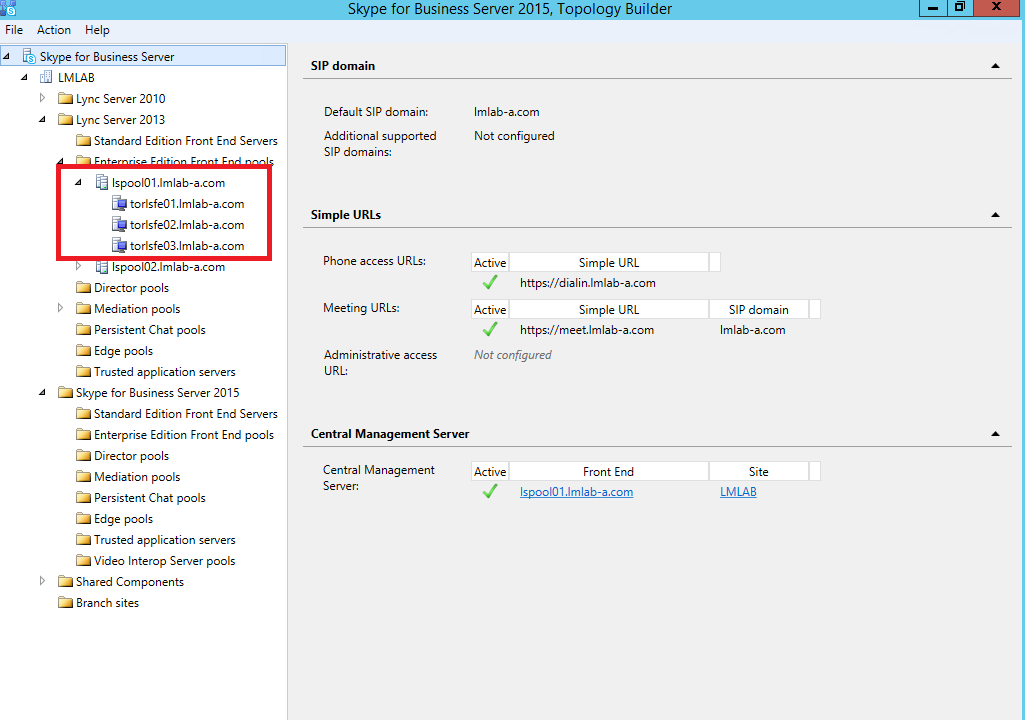
After downloading the topology, confirm that all the pools, services are correctly displayed. As mentioned above we will be updating lspool01.lmlab-a.com which has 3 front-end servers.
STEP 2: Upgrade and publish topology using Topology Builder
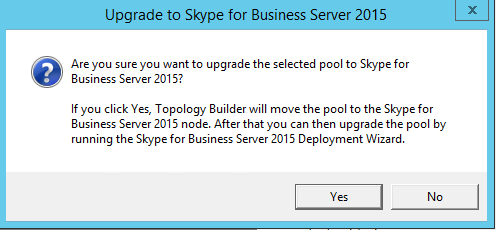
Upgrading the pool in the topology is very simple, this is achieved by right clicking the pool name and select Upgrade to Skype for Business Server 2015...
Now notice that the pool has moved from being a Lync 2013 pool to a Skype for Business Server 2015 pool. We can now go ahead and publish the topology.
Before proceeding with upgrading your front-end servers, confirm successful replication to all servers in your topology. Also confirm all services are running via the Lync Control Panel. Notice in the screen shot below, the "upgraded" pool shows a version of Unknown.
STEP 3: Upgrade Front-End Servers to Skype for Business
Before starting the upgrade process of your Enterprise Edition Pool you must disable the running services on all front-end servers in the pool. If you have more then 1 pool you can move your users to the secondary pool while you upgrade the primary.
Next run the following command in Lync PowerShell that will be upgraded.
Disable-CsComputer -Scorch
The above command will disable all the Lync 2013 services running on the front-end server. The -scorch switch will uninstall all the Lync 2013 services from the front-end server.
Remember to run this on every front-end server in the pool.
In the Services manager confirm that all the services are in a Disabled state and are not running.
Start the setup from your first front end server, check for updates to confirm the latest patches will be installed at the time of upgrade.
NOTE: As the In-Place Upgrade beings readiness checks will be performed. As I mentioned above to install the prerequisite hot fixes for each Server O/S version. If you do not, you will receive an error like this one.
As the upgrade wizard progresses through the process, you can see below the status of the upgrade. Also if you run into any issues during the upgrade process, you can close the upgrade wizard, fix the issue and resume the wizard and will pick back up from where it left off.
The upgrade wizard might require you to reboot the server while uninstalling the roles. Once you reboot and log back in the Skype for Business upgrade wizard will reopen automatically and continue with the process.
Once the upgrade is complete, the wizard will confirming that installation completed successfully.
STEP 4: Update Back-end Databases
After the upgrade process is complete, we need to upgrade the back-end SQL databases for the Enterprise Edition Pool. This is all done from PowerShell.
If this is an Enterprise Edition back-end and there are no collocated databases on this server
Install-CsDatabase -Update -ConfiguredDatabases -SqlFqdn "sqlbackend.domain.com"
If this is an Enterprise Edition back-end and there are collocated databases on this server (Archiving/Monitoring)
Install-CsDatabase -Update -ConfiguredDatabases -SqlFqdn "sqlbackend.domain.com" -ExcludeCollocatedStores
If this is a Standard Edition Server
Install-CsDatabase -Update -LocalDatabases
STEP 5: Start new Skype for Business Pool and Verify
After all the front end servers in the pool have been upgraded using the same process as described in this article and the back-end database has been upgraded, it is time to start the pool by running one single command.
Depending on the size of your front-end pool, and the number of routing groups within the front-end pool the start-up can take some time.
Once the command has completed, login to the Skype for Business Control Panel, click Topology and confirm that all services have started and replication is successful. Also login as a user that is homed on the Skype for Business pool and verify functionality.
I hope this upgrade how-to assists you in getting your environment moved to Skype for Business from Lync 2013. Over the next few weeks I will be posting more Skype for Business transition articles including SQL 2014 AlwaysOn.
Before starting the upgrade process of your Enterprise Edition Pool you must disable the running services on all front-end servers in the pool. If you have more then 1 pool you can move your users to the secondary pool while you upgrade the primary.
Next run the following command in Lync PowerShell that will be upgraded.
Disable-CsComputer -Scorch
The above command will disable all the Lync 2013 services running on the front-end server. The -scorch switch will uninstall all the Lync 2013 services from the front-end server.
Remember to run this on every front-end server in the pool.
In the Services manager confirm that all the services are in a Disabled state and are not running.
Start the setup from your first front end server, check for updates to confirm the latest patches will be installed at the time of upgrade.
NOTE: As the In-Place Upgrade beings readiness checks will be performed. As I mentioned above to install the prerequisite hot fixes for each Server O/S version. If you do not, you will receive an error like this one.
Also another common error during the upgrade will indicate that there are still services running in the pool that you are trying to upgrade. You MUST run the Disable-CsComputer -Scorch command on ALL front-end servers in the pool.
The upgrade wizard might require you to reboot the server while uninstalling the roles. Once you reboot and log back in the Skype for Business upgrade wizard will reopen automatically and continue with the process.
Once the upgrade is complete, the wizard will confirming that installation completed successfully.
At this point the first front end server has Skype for Business Server 2015 installed with all the same configuration and components as the when this server was a front-end in Lync 2013. All the new services are installed as shown below. Notice that the services have not yet been started. In Skype for Business Server 2015 a new command for starting the entire pool will be run after ALL front-end servers in this pool have been upgraded.
STEP 4: Update Back-end Databases
After the upgrade process is complete, we need to upgrade the back-end SQL databases for the Enterprise Edition Pool. This is all done from PowerShell.
Depending on your scenario run only ONE of the below commands:
If this is an Enterprise Edition back-end and there are no collocated databases on this server
Install-CsDatabase -Update -ConfiguredDatabases -SqlFqdn "sqlbackend.domain.com"
If this is an Enterprise Edition back-end and there are collocated databases on this server (Archiving/Monitoring)
Install-CsDatabase -Update -ConfiguredDatabases -SqlFqdn "sqlbackend.domain.com" -ExcludeCollocatedStores
If this is a Standard Edition Server
Install-CsDatabase -Update -LocalDatabases
STEP 5: Start new Skype for Business Pool and Verify
After all the front end servers in the pool have been upgraded using the same process as described in this article and the back-end database has been upgraded, it is time to start the pool by running one single command.
Open the Skype for Business Server Management Shell and type - Start-CsPool -PoolFqdn "poolname.domain.com"
Once the command has completed, login to the Skype for Business Control Panel, click Topology and confirm that all services have started and replication is successful. Also login as a user that is homed on the Skype for Business pool and verify functionality.
I hope this upgrade how-to assists you in getting your environment moved to Skype for Business from Lync 2013. Over the next few weeks I will be posting more Skype for Business transition articles including SQL 2014 AlwaysOn.
Thursday 23 April 2015
Skype for Business Server 2015 Protocol Workloads Poster and TechNet Library NOW AVAILABLE
Microsoft has published both the Technet Library Documentation and the Workloads Poster for Skype for Business
The TechNet Library can be found here - https://technet.microsoft.com/en-us/library/gg398616.aspx
The Protocol Workloads can be download from here: PDF Version or Visio Version
Keep and eye out for information and lab builds of Skype for Business including migrations from Lync 2010/2013 just after release day of Skype for Business Server.
The TechNet Library can be found here - https://technet.microsoft.com/en-us/library/gg398616.aspx
The Protocol Workloads can be download from here: PDF Version or Visio Version
Keep and eye out for information and lab builds of Skype for Business including migrations from Lync 2010/2013 just after release day of Skype for Business Server.
Skype Client UI in Skype for Business
Skype
for Business will still remain “lync.exe” from an executable
perspective and maintain the same major version number as Lync 2013.
Can I mix and match Lync 2013 and Skype for Business Clients
Yes you can, Lync 2013 clients will work on Skype for Business Server,
and Skype for Business Client will work on Lync 2013 Server.
Client Platform
|
Server Platform
|
Client UI
|
Lync 2010
|
Lync Server 2013
|
Lync 2010
|
Lync 2010
|
Skype for Business Server
|
Lync 2010
|
Lync 2013
|
Lync Server 2013
|
Lync 2013
|
Lync 2013 (no S4B update)
|
Skype for Business Server
|
Lync 2013
|
Lync 2013 (S4B update)
|
Skype for Business Server
|
Skype for Business
|
Lync 2013 (S4B update & EnableSkypeUI=FALSE)
|
Skype for Business Server
|
Lync 2013
|
Lync 2013 (S4B update & EnableSkypeUI=TRUE)
|
Skype for Business Server
|
Skype for Business
|
Lync 2013 (S4B update & EnableSkypeUI=NULL)
|
Skype for Business Server
|
Skype for Business
|
Skype for Business
|
Skype for Business Server
|
Skype for Business
|
Skype for Business (EnableSkypeUI=FALSE)
|
Skype for Business Server
|
Lync 2013
|
Skype for Business (EnableSkypeUI=TRUE)
|
Skype for Business Server
|
Skype for Business
|
Skype for Business (EnableSkypeUI=NULL)
|
Skype for Business Server
|
Skype for Business
|
In
order to control the Skype for Business/Lync 2013 User Interface, it must be
enabled via Client Policy. As customers have been requesting this update, I
suggest creating a new user based client policy and add some test users to the
policy so they can evaluate before providing to the remaining organization.
To create a new
Client Policy:
New-CsClientPolicy - PolicyName
SkypeUIClient - EnableSkypeUI $true
To enable users for this newly created policy:
Grant-CsClientPolicy -PolicyName SkypeUIClient
-Identity "user@company.com"
Subscribe to:
Posts (Atom)